
Drupal undoubtedly is the most secure CMS
that's exactly the reason you'll find most of the govt sites using Drupal.
If your website has ever been hacked, you know what a nightmare this can be, especially if your site is a requirement for your business. This is why when choosing a web content management platform that you make the right choice and hire the right company to build your website.
Drupal has a dedicated team of developers and contributors which constantly identifies, reports and patches security issues.
WordPress’ many plugins can have vulnerabilities and be easily hacked, particularly if the website owner doesn’t update to the latest version or the plugin gets old.
Drupal has a low number of vulnerabilities compared to Joomla, and the condition to exploit Drupal, in almost all cases, requires permissions typically granted to trusted users. Joomla, on the other hand, is more vulnerable not only because of the sheer number of exploits, but the severity, and the ability to trigger the exploit as an anonymous (unauthenticated) user.
The Drupal community is very serious about security and there is a Security Team that includes original creator Dries Buytaert and other major contributors to the platform.
India's (country with a population of 1.2 Billion) central govt. site India Portaland its sister sites which include National Informatics Centre and Government of India Department of Electronics and Information Technology use Drupal.
The White House is built with Drupal, US govt.
thinks Drupal as the most secure CMS
it’s pretty safe to say that you can too.
Complete Guide on Drupal Security
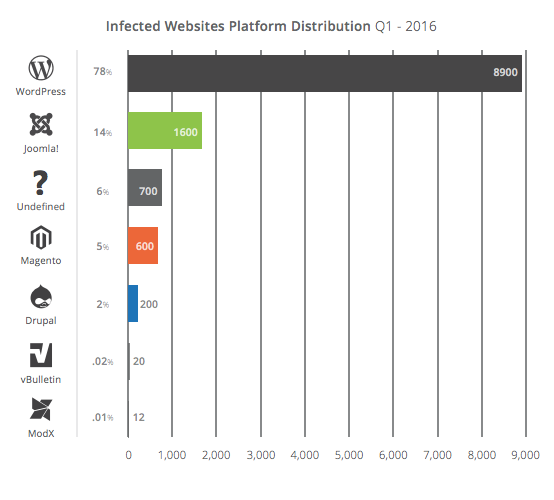
A recent report from Sucuri found that the vast majority of hacked websites are hosted on the WordPress CMS (content management system). Nearly 16,000 sites have been hacked in 2016. According to the report, “the three CMS platforms most being affected are WordPress, Joomla! and Magento.” But, the findings go on to say that these platforms are no more or less secure than Drupal, even though Drupal doesn’t even make the list.
That’s because security has more to do with humans than code. “In most instances, the compromises analyzed had little, if anything, to do with the core of the CMS application itself, but more with improper deployment, configuration, and overall maintenance by the webmasters and their hosts,” explains Sucuri.
THE PASSWORD IS...
The ways that people get hacked are, for the most part, straightforward. The worst offender is a bad password. The best passwords can’t be guessed and are a mix of letters, numbers and characters. But people's memory being what it is, most passwords are easy to remember, and as a result, easy to hack. Even if a user has a secure password, he might repeat it on a number of sites.
As soon as one site loses its data security, hackers will gain entry all over the web with that one frequently used password.
Another common problem is passwords that are shared across an organization, but remain unchanged when an employee leaves. If the former staffer was fired, or has had a negative experience with the company, there’s a chance that the password will fall into enemy hands.A site that stores valuable user information (such as credit cards or personal data) is especially at risk.
While the employee herself may not pose a security threat, a bad actor such as a relative or neighbor could gain access to credentials and wreak havoc. Give permissions only to trusted users, and have protocols in place for removing access for ex-employees. It’s a good idea to set up password constraints (must contain certain characters). Some companies set up automatic expiration, in which employees are required to reset their passwords every 60 days, but this is a debated idea. Many argue that forcing password changes is not a great plan since change is hard on the memory, so people tend to use easier passwords when forced to switch frequently. If a password is good, then changing it only mitigates issues but doesn’t completely eliminate them.
PLUGINS, MODULES AND HOSTS
The code underlying WordPress gets a lot of attention and is often fixed so vulnerabilities are more often in plugins. The Slider Revolution (AKA RevSlider) and GravityForms plugins have provided opportunities for hackers to get into a site and facilitate the installation of malware on visitors’ computers. While fixes for these gaps have been put in place, there will always be another vulnerability around the corner. It’s a game of cat and mouse.
Then there are other ways to hack into an account that have nothing to do with the CMS. Was the site’s host account hacked? Historically, it’s been too easy to call a provider’s customer service, provide the bare minimum to the customer service rep, and get into the backend of the site. That’s not technical, and there’s no need to be a skilled hacker. Fortunately, service providers are getting smarter about these schemes.
DRUPAL VS. WORDPRESS?
Drupal’s security relies upon a strong, coordinated effort. In general, Drupal is more secure overall, with a dedicated security team that operates using a series of protocols and a chain of responsibility for handling issues. As a Drupal shop, Zivtech receives weekly emails with alerts about security updates. Your CMS may do the same. Be sure to check.
Drupal is built upon rigorous coding standards, with tools to ensure that strict security practices are followed. The entire system is designed to make sure that all code that accesses the database is sanitized.
BEST PRACTICES FOR DRUPAL SECURITY
There are ways that you can audit your site to check that you are being cautious. Drupal has specific protocols, such as ensuring that the files on the file system are safe and set up properly and that an outside system can’t connect to the database.
First, make sure you have an SSL certificate. You can get them for free at Let’s Encrypt.
Next, if you’ve already taken all the standard steps to secure your site but still want to go a little further, you can also delete all readme text files that come with your CMS. This will reduce the surface area for an attack. By default, the readme files are accessible by anyone who visits your site. This could be a problem if an issue was discovered in a specific version of Drupal or a Drupal module. You can imagine that if there was a hack against Drupal version 7.10, hackers would scan sites for the 7.10 CHANGELOG.txt file to create a list of targets. Reduce that risk by deleting those files, or make them impossible to read over the internet.
Fending off security attacks is like playing hide and seek with frequently shifting rules. The developers behind the most popular CMS platforms work tirelessly to keep up. The primary reason that WordPress sites are attacked more frequently is actually all about the numbers. It's the most popular CMS, and therefore the most vulnerable.
